
Over the last decade, the rise in cyber attacks on manufacturing facilities and critical infrastructure has resulted in cyber security becoming a central concern amongst industrial automation and control system users and vendors.
With the convergence of information technology (IT) and operational technology (OT) in industrial manufacturing, there is a need to safeguard data access from the enterprise all the way down to the device level.
The following article, by Glenn Schulz of FDT Group and Katherine Voss of ODVA, describes efforts by the automation industry to develop next generation standards and technology, which enhance security throughout the lifecycle of industrial control devices in today’s connected world.
Introduction
As factory and plant operations become more connected in the era of the Industrial Internet of Things (IIoT) and Industrie 4.0, industrial organizations are making significant security investments to help protect their intellectual property, operations, and corporate image.
In the past, industrial control networks were primarily isolated systems, running proprietary protocols, using specialized hardware and software. But the industrial architecture has transformed over time, with collaborative mechanisms that involve internal and external integration.
Industrial facilities have traditionally relied on logical or physical security to protect their perimeter. These defenses range from firewalls to gates, guards and fences. However, any breach in perimeter security can put the facility’s industrial control system (ICS) at serious risk of denial-of-service (DoS) attacks or other disruptions.
Many plant sites employ a defense-in-depth security architecture to secure their ICS. This strategy is based on the idea that multiple layers of security are more resilient to attack. The expectation is that any one layer could be compromised at some point in time while the automation devices at the innermost layer would remain secure.
However, as attackers become more sophisticated, it becomes more important for the connected end device — the final layer of defense — to defend itself.
Evolving security challenges
Industrial security presents a difficult challenge in the age of open systems, increased connectivity and expanded data sharing. The fourth industrial revolution brings new cyber risks for plant and factory automation platforms. It is imperative for cyber security strategies to be secure, vigilant and resilient, as well as fully integrated into flexible business models.
As cyberspace shrinks due to the benefits derived from greater data exchange, new vulnerabilities in the ICS arise and new threats emerge. Left unchecked, the ICS, its devices and the networks to which they are connected, can be exploited by threat actors and pose potentially negative impacts on the safe, reliable and/or secure operation of production processes.
Governments and the private sector alike have expressed concern about cyber security vulnerabilities within automation systems. Regulatory bodies have identified threats to critical infrastructure where industrial Ethernet networks, such as EtherNet/IP, are commonly used. From a business standpoint, industrial firms are facing growing challenges from ransomware and other cyber threats.
With increasing reliance on connected systems, and ever-increasing amounts of data, it becomes more important for the systems, their devices, the data and points of connectivity to be inherently secure. Manufacturing plants have to give serious consideration to policies dictating how sensors and other edge devices can be accessed from the outside world.
One of the biggest concerns for end users is the industrial equipment lifecycle, particularly as it relates to the protection of data and access to crucial instruments. They must find ways to effectively address cyber security demands and protect plant assets such as field instruments, sensors and input/output (I/O) devices. A key issue is managing access to devices and their digitized artifacts over the entire lifecycle in a secure and reliable way.
Advancing industry standards
International standards bodies concerned about disruptive and dangerous cyber security attacks on plants and critical infrastructure operations have already established guidelines, standards and policies to help mitigate risks of cyber security threats to industry. In addition, governmental agencies such as ICS-CERT with the US Department of Homeland Security are working with industrial enterprises to identify threats.
ODVA, a global standards development and trade organization, develops and maintains the Common Industrial Protocol (CIP), an open communication protocol designed for automation and data use cases in industrial control systems and used by EtherNet/IP, the world’s largest industrial Ethernet network, and found in devices across diverse segments of the automation market.
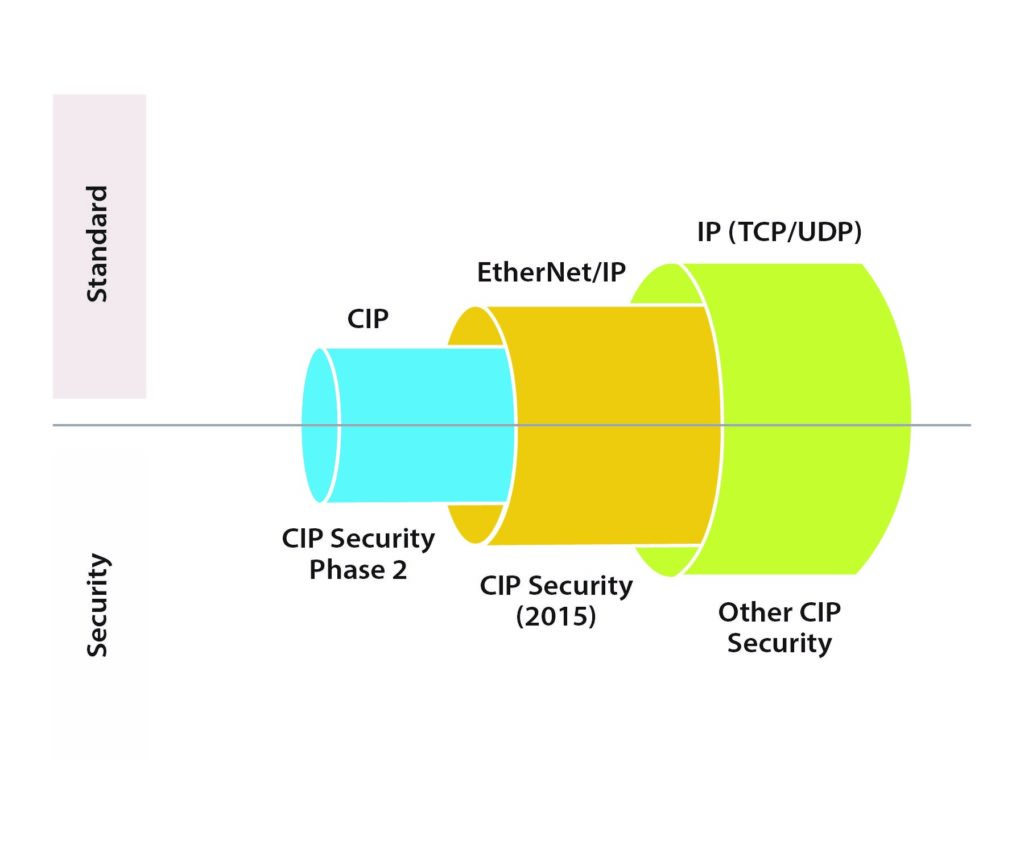
ODVA’s Roadmap for CIP Security
CIP Security, first released by ODVA in 2015, allows users to take additional steps to protect their ICS with techniques for securing transport of messages between EtherNet/IP devices and systems, and thus reduce their exposure to cyber security threats. The goal of CIP Security is to enable the EtherNet/IP device to protect itself from malicious communications. ODVA’s roadmap for CIP Security call for capabilities to be released in phases as shown in Figure 1. The first phase of CIP Security provides mechanisms to encrypt the transport of messages between EtherNet/IP ports and for certificates. In addition, recognizing that every EtherNet/IP device and system does not need to provide the same level of support for all defined security features, CIP Security defines a Security Profile to allow for a scalable solution. A Security Profile is a set of well-defined capabilities to facilitate device interoperability and end user selection of devices with the appropriate security capability. In the next phase of CIP Security, capabilities will be added around role-based authentication and authorization and enhanced encryption methods.
On the integration side of the automation industry, FDT Group is an international, non-profit corporation providing an open standard for enterprise-wide network and asset integration. The organization was founded for integration and lifecycle management of devices. Ongoing advancement of FDT technology is leveraging major developments like the IIoT and Industrie 4.0 to enable end users to realize the true potential of decentralization, interoperability, integration, as well as a unified view of all data and functions across process, factory and hybrid control applications.
FDT was built to support a comprehensive, open architecture for the connected world of industrial automation networks and assets. It supports the current installed base, and will adapt to future technologies and protocols. FDT/FRAMEs and Device Type Managers (DTMs) based on the current FDT specifications (FDT 2.0) are digitally signed, providing tamper-proof software delivery and non-repudiation. Granular DTM security with enhanced user rights is added to the security settings.
Ongoing industry collaboration
ODVA and FDT Group are both working to address cyber security vulnerabilities with on-going enhancements to their technologies and standards. The two organization’s have collaborated on the ability to integrate devices implementing ODVA technologies and standards into the FDT ecosystem for more than 10 years. The latest work resulted in a CIP annex supporting FDT 2.0, which allows for seamless tunnelling through industrial networks.
ODVA is one of the first standards development organizations to publish a true security overlay on an industrial network protocol. CIP Security utilizes standard encryption mechanisms and cryptographic keys to provide scalable security on the wire. This approach is in response to recognition that every device in a production system is potentially a point of attack. With the growing use of EtherNet/IP within the ICS, there is a corresponding proliferation of malware into control networks and distributed assets.
As part of CIP Security, security on the wire will allow for end devices to defend themselves from unauthorized and/or malicious access — a critical capability with the move towards more connected systems. End users will have a choice of features they need to secure their particular environment. Because of the nature of typical workflows, devices will, in most cases, have CIP Security off by default and users will need to enable it. They will then have the option of more simple methods such as use of pre-shared keys for device authentication, or more sophisticated mechanisms like x.509 certificates. This will allow for the creation of a single zone of trust for devices, or multiple zones, depending on the application requirements.
FDT Group, at the same time, is focused on incorporating methodologies and workflows into its standard to support emerging security requirements. The organization is compiling a series of best practices to help manufacturers implement FDT solutions in a way that avoids possible threat vectors. In addition to an Audit Team to provide an independent perspective on security enhancements, it has established an Incident Response Committee to help ensure timely communication for active issues and provide a vision for long-term security activities, as well as a technical group within the Architecture and Specification Team responsible for a security framework for the development of new specifications and tools.
From FDT Group’s perspective, any device that wants to communicate on a control network must be part of an established security model. Devices such as I/O cards, transmitters, etc. need to have awareness of the network’s security provisions and be able to participate in them. The same holds true for various software applications and tools.
To extend its support for the IIoT and Industrie 4.0, and simplify the automation ecosystem exchange, FDT Group is developing the FDT Server solution based on FDT3. The FDT Server enables mobility, cloud, and fog enterprise applications, as well as sensor-to-cloud and enterprise-wide connectivity employing FRAME and DTM business logic at the heart of its client-server architecture. The Server solution features robust layered security, leverages vetted industry standards, and utilizes transport layer security (TLS) to establish a hardened shell and encrypt all communications throughout the architecture. Optionally, this solution can authorize devices that connect to the Server. User-based security is employed to determine the user’s role and rights within the application.
The addition of security on the wire to the FDT standard will enable a complete solution for comprehensive, end-to-end, enterprise-wide security.
Forward-thinking approach
As established international standards development organizations representing many of the world’s leading suppliers of devices used in industrial control systems, ODVA and FDT Group have key roles in advancing end-to-end security for the connected enterprise, and in supporting the development of technologies and standards for security on the wire.
ODVA and FDT Group are committed to optimizing the industrial device lifecycle with robust built-in security features. Other potential collaboration between the two groups involves the security and authentication of tools and digitized artifacts within the FDT domain. This encompasses ODVA member suppliers utilizing DTMs in their field devices.
The next update to the CIP annex will embed CIP Security for seamless security integration and scalability of security control. The FDT Server will natively support CIP Security to allow for security on the wire in a scalable format. It will link the IT and OT security architecture with control from the FDT/FRAME-enabled system. Security on the wire will enable the ICS to defend itself from unauthorized and/or malicious access.
When the ICS and its connected assets have inherent protection from cyber security threats, there is the possibility of access from other trusted systems that might otherwise be considered part of an untrusted IT system. Conversely, devices may be able to produce data that can flow more directly and securely to IT systems.
One issue for industrial organizations is that production systems, and the assets (devices) within those systems, have very long lifecycles. Some devices may allow for field updates with new security capabilities. In other cases, the user would be looking at systems with varying degrees of device-level security. Tools such as firewalls or security proxies may be employed to help secure less-capable devices.
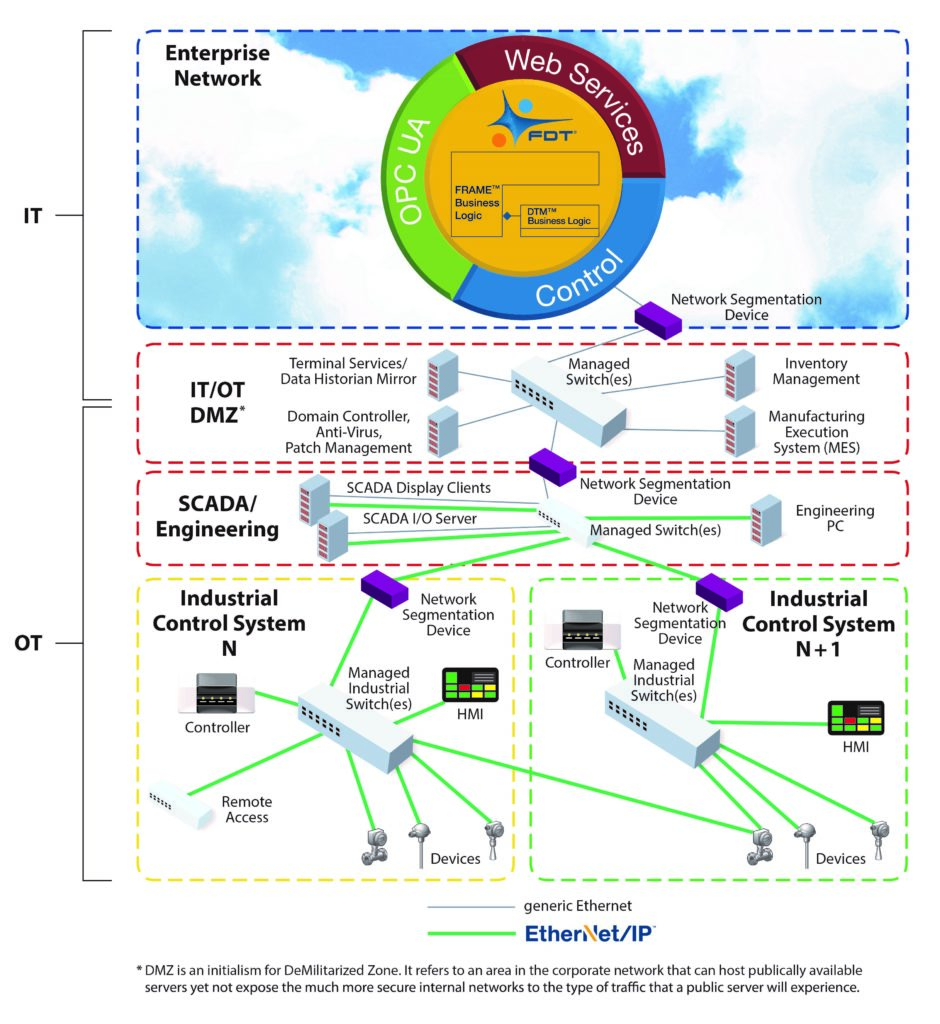
Converged IT/OT cyber security solution for the industrial enterprise
Ultimately, security on the wire will be implemented across the entire enterprise, from business systems down to the lowest device level. Any “open wire” will be regarded as a vulnerability and handled accordingly. As shown in Figure 2, technologies and standards, such as FDT3 and CIP Security, will provide users with a converged IT/OT cyber security solution for the industrial enterprise.
Conclusion
Industrial security is a complicated, multifaceted challenge that cannot be solved by simply purchasing the latest technology. Instead, managing the security of an industrial control network requires changing processes and managing risk.
ODVA and FDT Group share a similar vision for enhancements to ICS security technology. They recognize that is crucial to secure the control network itself in a changing cyber security environment. Indeed, every automation industry stakeholder must be aware of the crucial aspects of security throughout the lifecycle of industrial control devices in a connected enterprise ecosystem.
Advancements such as control on the wire offer the opportunity for self-protected devices, which add another dimension of security to the industrial network hierarchy.